Post-Quantum Cryptography: Building Quantum-Resistant Defences Before “Q-Day”

From Physics to Math: Why We Still Need New Keys
Previously we introduced quantum cryptography, especially Quantum Key Distribution (QKD), which uses the laws of physics to spot eavesdroppers on a fibre-optic link. QKD is powerful, but it can’t protect data already stored in the cloud, databases replicated worldwide, or every TLS session started before quantum links reach us all. For that we need post-quantum cryptography (PQC): classical algorithms that run on today’s CPUs yet remain secure even against a cryptographically relevant quantum computer.
What Exactly Is Post-Quantum Cryptography?
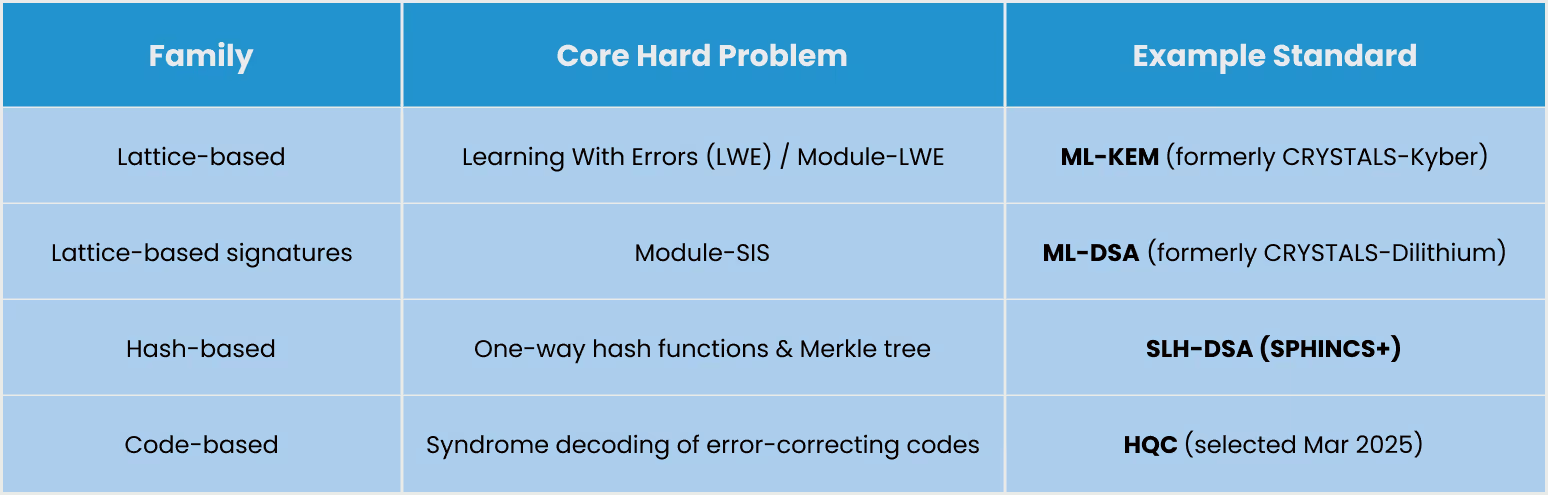
PQC replaces the hard mathematical problems that RSA and elliptic-curve crypto rely on (integer factorisation and discrete logarithms) with new problems that are believed to stay hard for both classical and quantum computers. Most candidates are based on:
The New Standards You Need to Know
After a seven-year competition, NIST finalised the first three PQC Federal Information Processing Standards on 13 Aug 2024:
- FIPS 203 – Module-Lattice-Based Key-Encapsulation Mechanism (ML-KEM, Kyber)(NIST)
- FIPS 204 – Module-Lattice-Based Digital Signature (ML-DSA, Dilithium)(NIST Computer Security Resource Center)
- FIPS 205 – Stateless Hash-Based Digital Signature (SLH-DSA, SPHINCS+)(NIST Computer Security Resource Center)
In March 2025 NIST announced that the code-based scheme HQC would also be standardised, filling a diversity gap in the portfolio.(NIST Computer Security Resource Center)
Why the Clock Is Ticking
Agencies such as CISA and the NSA warn of “store-now, decrypt-later”: adversaries who hoover up encrypted traffic today and wait until quantum machines can break RSA tomorrow. Tech outlets dub the moment those machines arrive “Q-Day.”(WIRED) Because migration of every certificate, firmware image and embedded device can take a decade, NIST urges organisations to phase out RSA/ECC by 2030–2035.(Netmeister)
Early Movers in Industry
Major vendors are already rolling PQC into products:
- Cloudflare is enabling Kyber-based tunnels across all IP protocols by mid-2025, at no extra cost to customers.(Barron's)
- Apple, Google and Mozilla test hybrid TLS (ECDHE + Kyber) in production browsers to gain real-world performance data.
- VPN makers such as OpenVPN and WireGuard have experimental Kyber and HQC branches.
These deployments prove that PQC can coexist with today’s stacks while ironing out performance kinks.
Transition Strategy: Five Practical Steps
- Inventory & Classify
Map every place your organisation creates, stores or transmits cryptographic material, including servers, IoT devices, backups. - Adopt Crypto Agility
Use libraries and protocols that let you swap algorithms via configuration, not firmware reflashes. Designing for agility now means you can roll forward again if weaknesses emerge.(ISACA) - Start With Hybrid Modes
Pair RSA or X25519 with Kyber or HQC in the same handshake. Even if one side is compromised, you still retain classical security today and quantum security tomorrow. - Pilot & Benchmark
Measure handshake latency, message sizes and CPU overhead in a test environment. Lattice schemes are fast, but signatures such as SPHINCS+ are bigger; plan bandwidth accordingly. - Update Governance & Vendor Contracts
Require suppliers to publish a PQC roadmap and conform to FIPS 203–205 by 2026 in new procurements.
Challenges on the Road Ahead
- Key and Signature Sizes: Kyber-768 public keys are ~1.1 KB, tiny versus many PQC peers but still larger than ECC. SPHINCS+ signatures can exceed 16 KB.
- Hardware Acceleration: Vector instructions (AVX-512, ARM SVE) help, but IoT MCUs may struggle.
- Long-Lived Roots: Updating root certificates baked into millions of devices (cars, TVs, medical implants) is a logistical headache; start now.
Looking Beyond Algorithms
PQC, QKD and QRNG are complementary:
- QRNG supplies true entropy for key generation.
- QKD distributes symmetric keys with eavesdropper detection for ultra-high-security links.
- PQC secures everything else over the public internet and protects stored data.
A layered approach ensures resilience even if one component is weakened.

Final Thoughts
Post-quantum cryptography is no longer a research curiosity; it is standardised, implementable and already shipping in mainstream products. Waiting until quantum computers hit cryptographic lift-off risks data you are sending today. Begin inventorying, testing hybrid handshakes and demanding PQC compliance from vendors. When Q-Day dawns, the organisations that planned ahead will simply rotate keys and carry on. Those that did not may wake to find their secrets laid bare.
The quantum era promises breakthroughs and, without PQC, breakthroughs for attackers too. The time to act is now.
References
Cloudflare. (2025, March 30). Quantum‑safe Zero Trust with Cloudflare’s WARP client‑to‑tunnel configuration. https://blog.cloudflare.com/post-quantum-zero-trust/
Cybersecurity and Infrastructure Security Agency, National Security Agency, & National Institute of Standards and Technology. (2023, August). Quantum‑readiness: Migration to post‑quantum cryptography (Publication No. CISA‑23‑QRC). https://www.cisa.gov/sites/default/files/2023-08/Quantum%20Readiness_Final_CLEAR_508c.pdf
National Cyber Security Centre. (2025, February 28). NCSC guidance sets 2035 deadline for migration to post‑quantum cryptography. https://www.ncsc.gov.uk/
National Institute of Standards and Technology. (2024, August 13). FIPS 203: Module‑Lattice‑Based Key‑Encapsulation Mechanism (ML‑KEM). U.S. Department of Commerce. https://doi.org/10.6028/NIST.FIPS.203
National Institute of Standards and Technology. (2024, August 13). FIPS 204: Module‑Lattice‑Based Digital Signature Algorithm (ML‑DSA). U.S. Department of Commerce. https://doi.org/10.6028/NIST.FIPS.204
National Institute of Standards and Technology. (2024, August 13). FIPS 205: Stateless Hash‑Based Digital Signature Algorithm (SLH‑DSA). U.S. Department of Commerce. https://doi.org/10.6028/NIST.FIPS.205
National Institute of Standards and Technology. (2025, March 17). NIST selects HQC as fifth algorithm for post‑quantum encryption. https://www.nist.gov/news-events/news/2025/03/nist-selects-hqc-fifth-algorithm-post-quantum-encryption



