Your Encryption Is Only as Strong as Your Randomness: Here’s the Secret Fix

The Secret Sauce of Secure Encryption: Randomness
Random numbers are the backbone of encryption. When organisations use weak sources of randomness for cryptographic applications, it gives rise to serious vulnerabilities, as we will see later in this post. But, have you ever wondered, how does one quantifies the quality of a source of random numbers? Traditionally, that’s where entropy comes in; it measures how surprising the data is. The higher the entropy of a set of random numbers, the harder they are to predict.
However, when using random numbers for critical applications such as encryption, we must go beyond surprise. For random numbers to be secure, we demand that they be uniform, private, and unpredictable. Random numbers that satisfy these requirements are information-theoretically secure, meaning that the best strategy an adversary can take is to make a random guess of the numbers.
Weak Randomness is a Security Risk
In a world that is increasingly digitalised, cybersecurity is of paramount importance, and randomness is no longer just a technical detail; it's a cornerstone of modern cryptography. Randomness plays a critical role across a wide range of security algorithms, ensuring confidentiality, integrity, and authenticity of digital communications.
But what happens when randomness is weak?
Cryptographic algorithms like Digital Signature Algorithm (DSA) and Elliptic Curve Digital Signature Algorithm (ECDSA) could leak key material if the random numbers are even slightly predictable. The most widely used encryption mode, Galois/Counter Mode (GCM), fails catastrophically if a symmetric key and nonce are ever reused. Rivest-Shamir-Adleman (RSA), often the alternative to DSA, also suffers when its random numbers are predictable due to improper seeding of random number generators.
A Decade of Broken Keys
A steady stream of research has exposed cryptography’s fragility due to weak randomness:
2012: Researchers cracked 26,965 RSA keys using simple math (GCD computations) against known public keys, tracing the flaw to predictable RNG output during Linux system startup. (Issue unpatched even after 2016)
2019: At least 435,000 certificates were generated with weak sources of randomness, making their prime factors discoverable and the keys vulnerable to compromise.
2024: In PuTTY versions 0.68–0.80 (fixed in 0.81), masking the most significant byte during random number generation of the ECDSA nonce for the NIST P-521 curve introduced a statistical bias, allowing an attacker to recover a user’s private signing key from roughly 60 signatures.
They reveal a systemic problem: when the quality of random numbers is low, security crumbles. All cryptographic algorithms need to be built upon high-quality randomness to ensure security.
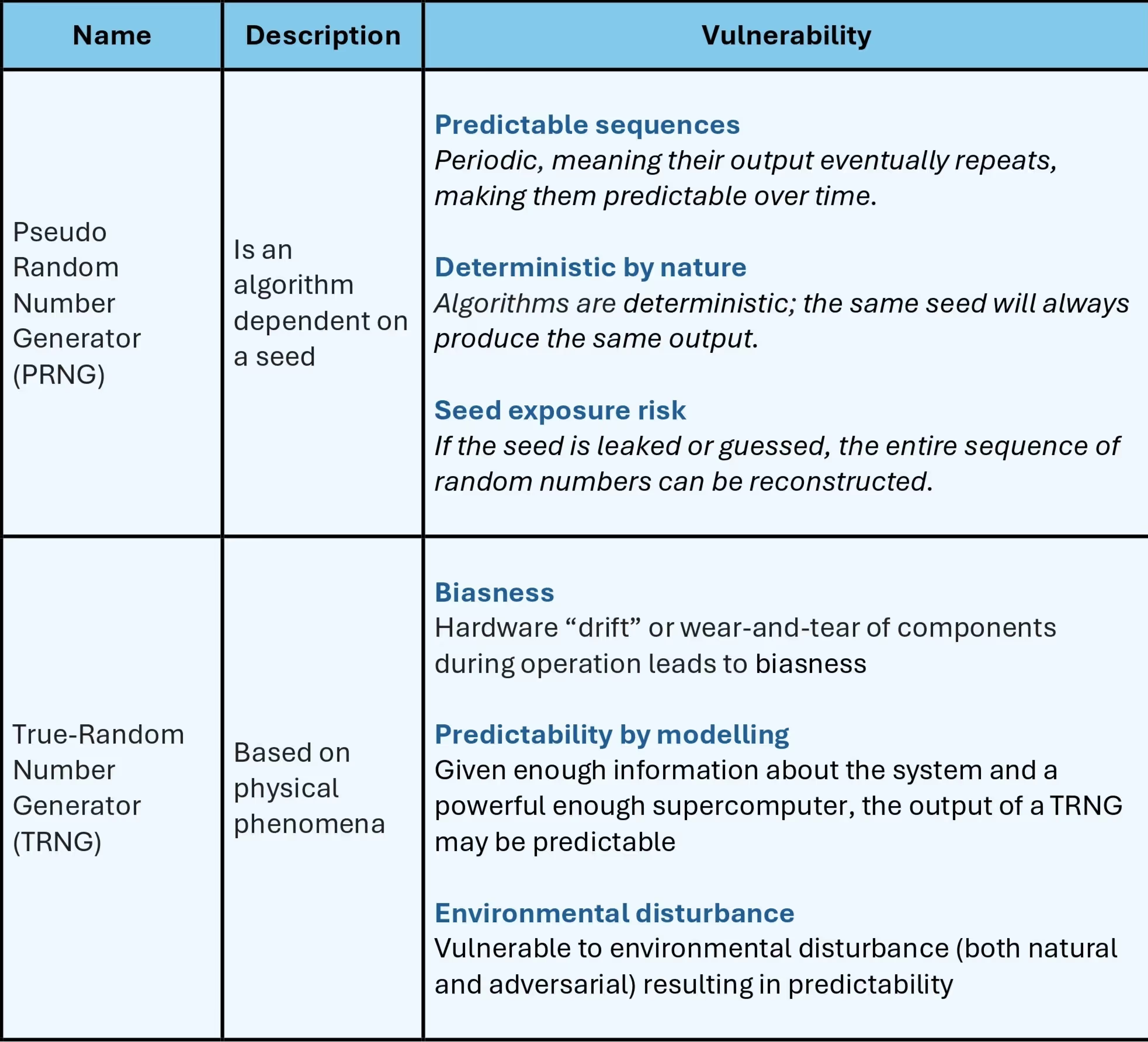
Cracking the Code: Vulnerabilities of Classical RNGs
Classical random number generators (RNGs) are broadly split into two categories, pseudo-random number generators (PRNGs) and true random number generators (TRNGs). Let us discuss them in the following table.
Randomness Powered by Quantum Physics: Quantum Random Number Generator (QRNG)
What is a QRNG, and why are they better than classical RNGs?
Unlike classical RNGs, a Quantum Random Number Generator (QRNG) is a device that leverages the principles of quantum mechanics to produce random numbers that are uniform, private, and unpredictable. These random numbers are a result of fundamentally indeterministic quantum processes.
This makes the output of a QRNG:
- Unpredictable: Even if any party has complete information about the QRNG, he/she will not be able to accurately predict the output.
- Information-theoretically secure: The security of the output can be expressed and quantified mathematically.
By contrast, in addition to the vulnerabilities discussed in the table above, it is not possible to express the security of PRNGs and TRNGs in an information-theoretic manner.
So, as long as one uses a QRNG, then one should have access to high-quality random numbers, right? Unfortunately, not quite. QRNGs also have different levels of security. Currently, QRNGs that are commercially available rely on trusted devices. This means that the security is derived based on accurate characterisation and modelling of the inner workings of the components of the QRNG. This approach has drawbacks, because components drift during their continuous operation, and adversarial attempts to control the devices cannot be detected.
QDICE® QRNG: Delivering Random Numbers with Unparalleled Security
The advantage of QDICE® QRNG
Squareroot8’s QDICE® QRNG surpasses commercially available QRNGs in terms of its security. At its core is our patented and trademarked Quantum Detector-Device-Independent Certification of Entropy (QDICE®) technology. As the name suggests, no assumptions are made regarding the inner workings of the detector. The QDICE ® QRNG verifies that the random numbers obtained are of a quantum origin and detects potential adversarial attacks on the detector.
QDICE® QRNG therefore delivers random numbers that are uniform, private, and unpredictable using fewer assumptions as compared to PRNG, TRNG, and current commercially available QRNGs.
The magic behind QDICE® QRNG
Squareroot8’s QDICE® QRNG is built upon our proprietary protocol that implements quantum detection self-testing. This means that our QDICE® QRNG receives inputs and performs tests probabilistically during its operation. Using the gathered input-output statistics of these test rounds, the QDICE® QRNG certifies that the random numbers generated are information-theoretically secure. Such a notion is important because it certifies that the random numbers generated are independent from any other system in the world.
Final Thoughts
Squareroot8’s QDICE® QRNG sets a new standard in randomness, delivering uniform, unpredictable, and private random numbers while making less assumptions. This is a feature that has been elusive from classical random number generators and current QRNGs in the market. With QDICE®, you gain the advanced security needed to stay ahead of today’s evolving threats.
So, step confidently into the future of cutting-edge random number generation. Experience Squareroot8’s QDICE® QRNG today.
Unlock the Era of QDICE® QRNG Now: Where Randomness Meets Unmatched Security



